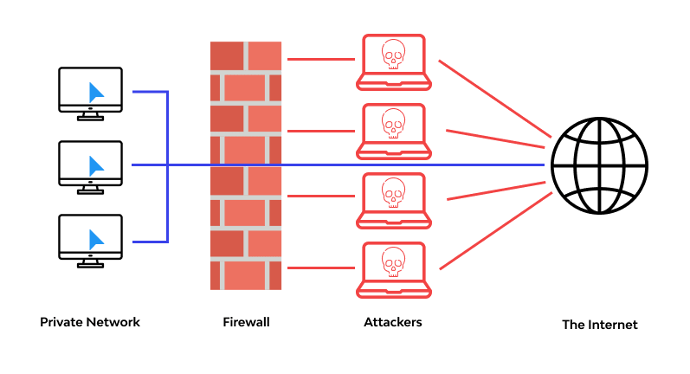
A Firewall is a network security device that monitors and filters incoming and outgoing network traffic based on an organization’s previously established security policies. At its most basic, a firewall is essentially the barrier that sits between a private internal network and the public Internet. A firewall’s main purpose is to allow non-threatening traffic in and to keep dangerous traffic out.

A Firewall is a necessary part of any security architecture and takes the guesswork out of host level protections and entrusts them to your network security device. Firewalls, and especially Next Generation Firewalls, focus on blocking malware and application-layer attacks, along with an integrated intrusion prevention system (IPS), these Next Generation Firewalls can react quickly and seamlessly to detect and react to outside attacks across the whole network. They can set policies to better defend your network and carry out quick assessments to detect invasive or suspicious activity, like malware, and shut it down.
Firewalls, especially Next Generation Firewalls, focus on blocking malware and application-layer attacks. Along with an integrated intrusion prevention system (IPS), these Next Generation Firewalls are able to react quickly and seamlessly to detect and combat attacks across the whole network. Firewalls can act on previously set policies to better protect your network and can carry out quick assessments to detect invasive or suspicious activity, such as malware, and shut it down. By leveraging a firewall for your security infrastructure, you’re setting up your network with specific policies to allow or block incoming and outgoing traffic.
A firewall sits at the perimeter of a protected network, and all traffic crossing that boundary flows through the firewall. This provides it with visibility into these traffic flows and the ability to block any traffic that violates the predefined access control list (ACLs) or is otherwise deemed a potential threat to the network.
A firewall is important because it acts as the network’s first line of defense. An effective firewall can identify and block a wide variety of threats, preventing them from reaching the internal network. This decreases the amount of malicious traffic that other security solutions must inspect and the potential threats faced by the internal network.
Firewalls can be classified in a few different ways. Three important concepts to understand when selecting a firewall solution are the difference between stateful and stateless firewalls, the various form factors in which firewalls are available, and how a next-generation firewall (NGFW) differs from traditional ones.
The oldest and simplest distinction between firewalls is whether it is stateless or stateful. A stateless firewall inspects traffic on a packet-by-packet basis. The earliest firewalls were limited to checking source and destination IP addresses and ports and other header information to determine if a particular packet met simple access control list requirements. This enabled firewalls to block certain types of traffic from crossing the network boundary, limiting their exploitability and ability to leak sensitive data.
Over time, firewalls grew more sophisticated. Stateful firewalls are designed to track details of a session from its beginning to its end. This enabled these firewalls to identify and block packets that don’t make sense in context (such as a SYN/ACK packet sent without a corresponding SYN). The greater functionality provided by stateful firewalls means that they have completely replaced stateless ones in common usage.
Traditional types of firewalls (stateful or stateless) are designed to filter traffic based upon predefined rules. This includes checking packet header information and ensuring that incoming or outgoing packets logically fit into the current connection’s flow.
A next-generation firewall (NGFW) includes all of this functionality but also incorporates additional security features. A NGFW adds additional security solutions such as application control, an intrusion prevention system (IPS), and the ability to inspect suspicious content in a sandboxed environment. This enables it to more effectively identify and block incoming attacks before they reach an organization’s internal network.

Another way to distinguish between different types of firewalls is based on how they are implemented. Firewalls generally fall into three categories:
Hardware Firewalls
These firewalls are implemented as a physical appliance deployed in an organization’s server room or data center. While these firewalls have the advantage of running as “bare metal” and on hardware designed specifically for them, they are also constrained by the limitations of their hardware (number of network interface cards (NICs), bandwidth limitations, etc.).
Software Firewalls
Software firewalls are implemented as code on a computer. These firewalls include both the firewalls built into common operating systems and virtual appliances that contain the full functionality of a hardware firewall but are implemented as a virtual machine.
Cloud Firewalls
Organizations are increasingly moving critical data and resources to the cloud, and cloud-native firewalls are designed to follow suit. These virtual appliances are specifically designed to be deployed in the cloud and may be available as either standalone virtual machines or as a Software as a Service (SaaS) offering.
Each of these different firewall form factors has its advantages and disadvantages. While a hardware firewall has access to optimized hardware, its capabilities can also be constrained by the hardware it uses. A software firewall may have slightly lower performance but can be easily updated or expanded. A cloud firewall, however, takes advantage of all of the benefits of the cloud and can be deployed near to an organization’s cloud-based resources.

The firewall has undergone a series of transformations as the evolution of enterprise networks and the cyber threat landscape have caused organizations’ security requirements to change. The latest of these changes is of course the increased adoption of cloud computing and remote work.
Cloud firewalls are a step in the right direction toward meeting enterprise cloud security needs. However, as enterprise networks continue to evolve, organizations will continue to move to deploy a next-generation firewall as part of an integrated Secure Access Service Edge (SASE) solution.
In general, a next-generation firewall is always the right choice for protecting an organization’s network. Beyond that, the details (such as the desired form factor) depend upon the organization’s business needs and the firewall’s intended deployment location.
For your network & internet technology solution get in touch with us
IPTEC is a professional solution company having prestigious clients all across South Sudan
Contact Sales
